Financial services organizations face a growing threat from cybercriminals that exploit security vulnerabilities in software systems to gain access to financial data and private information. Responding to this threat, the New York State Department of Financial Services (NYDFS) included specific language in the 23 NYCRR 500 regulation requiring financial companies to implement secure software development practices to combat software vulnerabilities.
In short, 23 NYCRR 500 requires regulated entities to implement a secure software development lifecycle (Secure SDLC) that prevents vulnerable code from being written or deployed. Since this regulation was rolled out in March 2017, Chief Information Security Officers (CISOs) and VPs of Development have wrestled with the best approach for implementing Secure SDLC in their organizations.
In this post, we look at how the Micro Focus Fortify platform can be used to implement a Secure SDLC that satisfies the requirements specified in 23 NYCRR 500.
NYSDFS Regulations Require Secure SDLC
The New York State requirements for Secure SDLC are contained in a comprehensive set of cybersecurity regulations for financial services companies published as 23 NYCRR 500. The portion relevant to software development is Section 500.08, as follows:
Section 500.08 Application Security.
(a) Each Covered Entity’s cybersecurity program shall include written procedures, guidelines and standards designed to ensure the use of secure development practices for in-house developed applications utilized by the Covered Entity, and procedures for evaluating, assessing or testing the security of externally developed applications utilized by the Covered Entity within the context of the Covered Entity’s technology environment.
(b) All such procedures, guidelines and standards shall be periodically reviewed, assessed and updated as necessary by the CISO (or a qualified designee) of the Covered Entity.
As specified in Section 500.08, financial services organizations need to adhere to secure development practices that prevent vulnerable software from being written. Secondly, financial services organizations need to have application security testing procedures that continue to probe all deployed software, alerting software developers to vulnerabilities that are uncovered at runtime, so these can be repaired. Thirdly, financial services organizations need to monitor their applications within the context of their own technology environment. Such real-time monitoring of the production environment should detect attempted attacks as they are occurring and alert operations management so that defensive action can be taken as needed.
The Micro Focus Fortify suite of products provides powerful tools that help your organization implement all three components of a secure SDLC: secure development practices, application security testing, and production threat monitoring.
Implementing a Secure SDLC with Micro Focus Fortify
Micro Focus has long been a leader in Gartner’s Magic Quadrant for Application Security Testing (AST). As you can see below, the company ranks in the upper right of the 2018 Leaders quadrant.
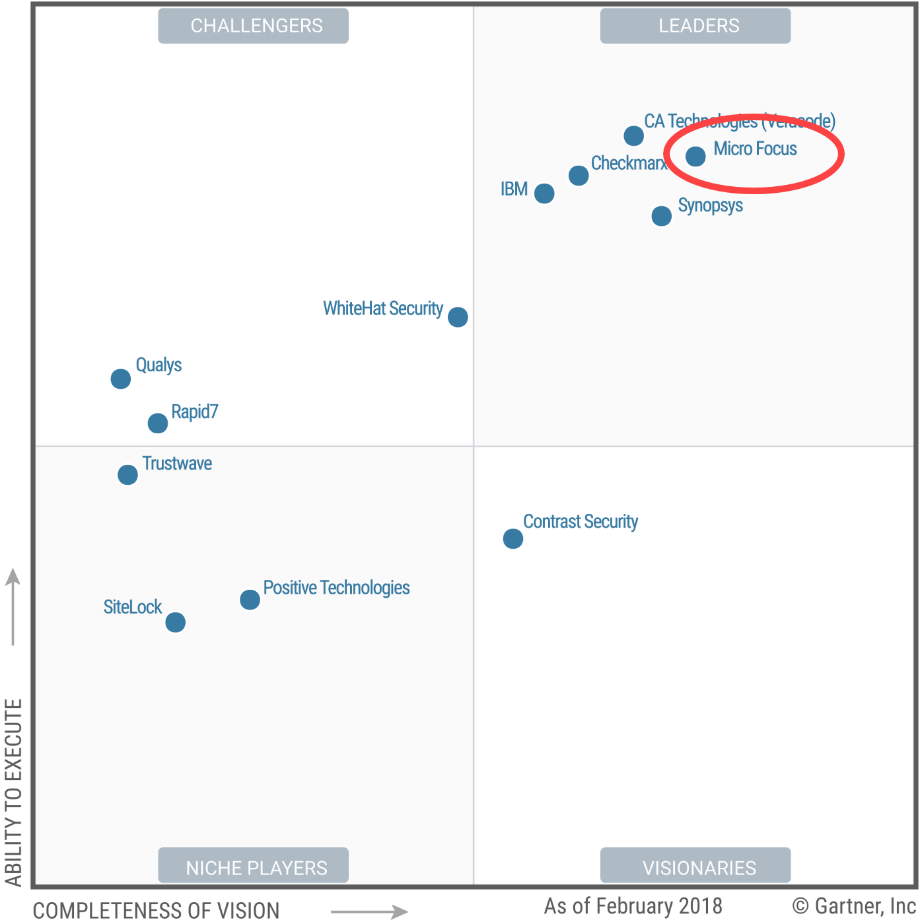
Gartner identifies three key components of application security that support compliance with New York State regulations:
- SAST (Static Application Security Testing) – technology that analyzes an application’s code to identify security vulnerabilities during the programming (development) phase of the SDLC.
- DAST (Dynamic Application Security Testing) – technology that analyzes applications while they are running during the testing or operational phases of the SDLC. DAST technology simulates attacks against an application and analyzes the results to identify vulnerabilities.
- RASP (Runtime Application Self-Protection) – technology that monitors activity at runtime, during the operational phase of the SDLC, identifies incoming threats, and enables protective action to be taken.
To use an American football analogy, you can think of these three components as the units of a football team. SAST is like a team’s offensive unit. This technology is pro-actively improving the software by eliminating vulnerabilities. On the other hand, DAST acts like a team’s defensive unit. This technology is attacking the software at runtime, probing for weaknesses, and trying to break through to access sensitive data. Lastly, RASP is like a special team unit. RASP is used less frequently than SAST or DAST but can play an important role at critical times like when hackers are actively trying to penetrate your system. RASP technology can identify the access attempt patterns used by hackers and act to thwart the intrusion.

Fortify Static Code Analyzer for SAST
Micro Focus delivers static application security testing (SAST) through the Fortify Static Code Analyzer (SCA). Fortify SCA detects security issues while developers are coding so that problems can be remediated immediately when they are least expensive to fix. Backed by the Fortify Software Security Research Group that monitors emerging threats, SCA is continually updated to recognize the latest vulnerabilities. The goal is to prevent vulnerable software from ever being written.
In this manner, Fortify SCA is used during the coding phase of the software development lifecycle (SDLC) and addresses the 23 NYCRR 500 requirement to have “secure development practices for in-house developed applications”. Because Fortify SCA provides immediate feedback to developers while they are coding, it helps to educate them about security while they work, enabling them to create more secure software.
How It Works
Fortify SCA uses a variety of algorithms, together with an extensive knowledge base of secure coding rules, to scan application source code for vulnerabilities. For example, SCA knows that data entry forms on the web must be coded with certain safeguards or else they can be vulnerable to SQL injection attacks. If SCA detects a form in the application code which lacks the proper safeguards, the developers will be alerted. This can happen in real-time, while the form is being coded. Or, it may be picked up by a batch scan that runs at predefined intervals.
Fortify SCA analyzes all execution paths through the code to identify vulnerabilities. Typically, the first time a codebase is scanned, numerous potential vulnerabilities will be found. Fortify SCA will rank the issues by seriousness of threat, so that developers can work on the most pressing issues first. The tool will also offer remediation guidance, indicating what actions a developer could take to eliminate the vulnerability. Fortify SCA can scan 25 different programming languages and detects more than 991 vulnerability categories.
Fortify WebInspect for DAST
While SAST provides a strong foundation for a secure SDLC, not all vulnerabilities can be determined by static code scans. In addition, much of the software deployed by an organization has been developed by third parties. Even internally written code is bundled with third party libraries, plugins, etc. As a result, dynamic testing is needed to support ongoing detection and remediation of production software vulnerabilities. To support ongoing application evaluation and testing, Microfocus delivers dynamic application security testing (DAST) through Fortify WebInspect. WebInspect automatically probes your software applications at runtime, testing for vulnerabilities, and alerting development and operations teams to correct any problems that are uncovered.
In this manner, Fortify WebInspect is used during the testing phase of SDLC and addresses the 23 NYCRR 500 requirement to have “procedures for evaluating, assessing or testing the security of … applications”. Because Fortify WebInspect can crawl modern frameworks (e.g., Java Spring) and web technology (e.g., Apache web server), it can detect vulnerabilities that arise from how code is deployed, how frameworks are configured, and from externally developed software.
How It Works
Fortify WebInspect mimics real-world hacking techniques to probe your applications for vulnerabilities. Known attack strategies (aka “attack vectors”) are applied to your application interfaces and responses are analyzed. Internal responses (e.g., stack traces, SQL queries) are monitored as well, searching for behavior that indicates a vulnerability. When a vulnerability is detected, Fortify WebInspect provides a detailed report about the underlying issue, the implications for security if it were to be exploited, and suggestions for remediation. The tool also leverages a comprehensive knowledgebase of configuration vulnerabilities and can scan your infrastructure to expose these vulnerabilities as well as problems at the application level.
Fortify Application Defender for RASP
SAST and DAST are the backbone of a secure SDLC and necessary to protect your data and financial systems from malicious intruders. But cybercriminals are getting smarter and can sometimes exploit new vulnerabilities before static or dynamic application testing tools have learned to check for them. For this reason, all financial services organizations can benefit from implementing a runtime application self-protection (RASP) system as well.
RASP technology provides centralized visibility of application use and abuse across all externally facing applications. When abusive behavior is detected (e.g., repeated probing of a specific interface with the same malformed request), a RASP solution can alert your operations and security teams to diagnose the threat. In addition, automated self-protective action can be taken (e.g., blacklisting IP addresses that are sending abusive requests) to eliminate the immediate vulnerability while your experts analyze the software and infrastructure to pinpoint any structural vulnerability that the hacker may have been trying to exploit.
Micro Focus delivers RASP via their Fortify Application Defender product. When deployed in your infrastructure, Application Defender instruments your applications to capture system and user activity logs. By monitoring these logs, it can detect and stop attacks in dozens of vulnerability categories such as SQL injection (SQLi) and cross-site scripting. Application Defender provides the “inside view” that code scans and external probes cannot access. In this manner, Fortify Application Defender is used during the production phase of SDLC and addresses the 23 NYCRR 500 requirement to be continually “assessing or testing … within the context of the … technology environment”.
Financial Companies Achieve Compliance using Micro Focus Fortify
Financial services organizations, banks, and insurance companies need to comply with New York State Department of Financial Services regulations. But it can be a challenge for CISOs and VPs of application development to find the best tools and procedures to achieve compliance.
If you are looking for a 23 NYCRR 500 compliance solution or upgrading one that you already have, the Micro Focus Fortify suite of products covered in this post should be at the top of your consideration list. In addition to being highly rated by Gartner, Micro Focus continues to innovate, bringing new technologies to market (e.g., Fortify Application Defender) and enabling you to build application security into the entire SDLC.
Since 23 NYCRR 500 is relatively new (March 2017), many financial services organizations have only recently wrapped up the process of developing the policies and standards needed for compliance. These documents can now serve as your guide to selecting the software tools you will use to implement and automate compliance activities.
When you do your evaluation, you will find that the Micro Focus Fortify suite has been designed for flexibility so that it can almost certainly accommodate your company’s policies and standards. Furthermore, Fortify allows you to implement a secure software development lifecycle (Secure SDLC) that prevents vulnerable code from being written or deployed thus satisfying the requirements specified in 23 NYCRR 500.
You can even run a free trial of the hosted product, Fortify on Demand, to determine how well the Fortify products would meet your company’s needs.
IIS - Your Partner for Micro Focus Solutions
International Integrated Solutions (IIS) is a Micro Focus Platinum Partner with extensive experience in the financial services vertical market. IIS can design, install, and maintain a secure software development lifecycle framework infrastructure for your organization.
IIS is also a distinguished HPE partner, winning HPE Global Partner of the Year in 2016 and Arrow’s North American Reseller Partner of the Year in 2017. They have worked with Fortify for many years prior to 2016 when it was part of the HPE portfolio and have continued to actively partner with Micro Focus since they acquired the technology.
As your service provider, IIS brings deep expertise and experience. Having solved a myriad of problems for hundreds of customers, they bring a holistic view of the datacenter that includes security as a component. IIS can help your organization make the best security decisions in the context of your existing datacenter infrastructure and applications.






