Few things can harm productivity in your enterprise more than poor WIFI performance. When the wireless network is slow, people cannot perform their jobs effectively. Sharing files, loading websites, replying to emails, or doing anything else requiring network connectivity is painful. For the IT organization, complaints of poor WIFI performance are also a huge burden. When users are affected, nothing else can get accomplished until IT fixes the problem, so WIFI issues get in the way of other priorities.
But there is one WIFI problem that’s worse than slow or dropped connections. That’s a security breach. Criminal hackers have exploited vulnerabilities in wireless access points to gain access to corporate networks and, from there, to the devices of other connected users as well as financial systems and customer data. Vulnerabilities can result from inherent flaws in WIFI security protocols as well as poorly configured security, vulnerable passwords, and weak encryption.IT departments in medium to large organizations face a complex task when providing ubiquitous WIFI access. As more organizations are moving to replace wired networks with WIFI, the challenge becomes increasingly important. In this post, we look at the steps needed to ensure both WIFI performance and security.
WIFI Performance Requires More than Great Coverage
Many organizations assume that if their wireless network provides adequate coverage then their users will experience good service. But, that is not always true. Great WIFI performance requires more than just great coverage. You also need to consider user density. For example, an auditorium full of users trying to connect can easily overwhelm a single access point, even if that access point provides complete coverage of the space.
In addition, when selecting access point locations, organizations need to be cognizant of the surroundings. While WIFI signals pass through drywall, plywood, and most building materials relatively easily, there are exceptions. Glass walls, metal, brick, and reinforced concrete can absorb or completely block WIFI signals. Water, such as in a large aquarium, can be particularly problematic because it absorbs the radio frequencies used for wireless networking communication. We had one client where we discovered that shelving containing bottles of perfume (mostly water) was causing severe degradation of WIFI coverage. In many cases, problems like this can be overcome by moving the access point or aiming the antennas. In the most extreme cases, different access points or antenna types may be necessary to provide the coverage spread desired.
Because of these potential complications, a physical assessment of the environment is recommended to design a high performance WIFI infrastructure. When we work with clients, IIS typically performs a predictive site survey as a first step. Building floor plans, access point types and locations are uploaded into a tool that suggests an optimal design and predicts coverage areas. The tool accounts for building materials, square footage, user density, types of applications, antenna models and other variables to generate a plan and predict performance. An onsite physical assessment would then be performed to validate the predictive design and determine access point placement, choice of antennas and antenna orientation to provide optimal performance.
HPE Aruba AirWave for WIFI Configuration and Management
HPE Aruba AirWave is one of the tools that we highly recommended for managing the Wi-Fi environment during and after installation, and for optimizing wireless network performance on an ongoing basis. AirWave proactively monitors the health and performance of all wireless devices connected to your network.
AirWave provides the ability to upload floor plans of your environment. The floor plans are then used in conjunction with data collected to generate heat maps showing the signal strength and coverage area throughout your organization. Red areas show where the signal is strongest, and blue are the weakest. Airwave uses the same data to automatically adjust signal strength based on user density to ensure the best coverage and performance. Using a heatmap like this, you can identify dead zones, interference points, and the location of access points. In addition to signal strength, multiple overlays can be used to visualize client health, traffic thresholds, unified communication calls (UCC), and channel utilization. Using this data, you can quickly diagnose client, building, floor, or location-specific issues.
The heatmaps can also be used to identify user density, as well as the physical movement of devices and clients. This can be useful to isolate and troubleshoot challenging intermittent mobility issues. Rogue access points and unauthorized devices can also be identified and located to ensure network security.
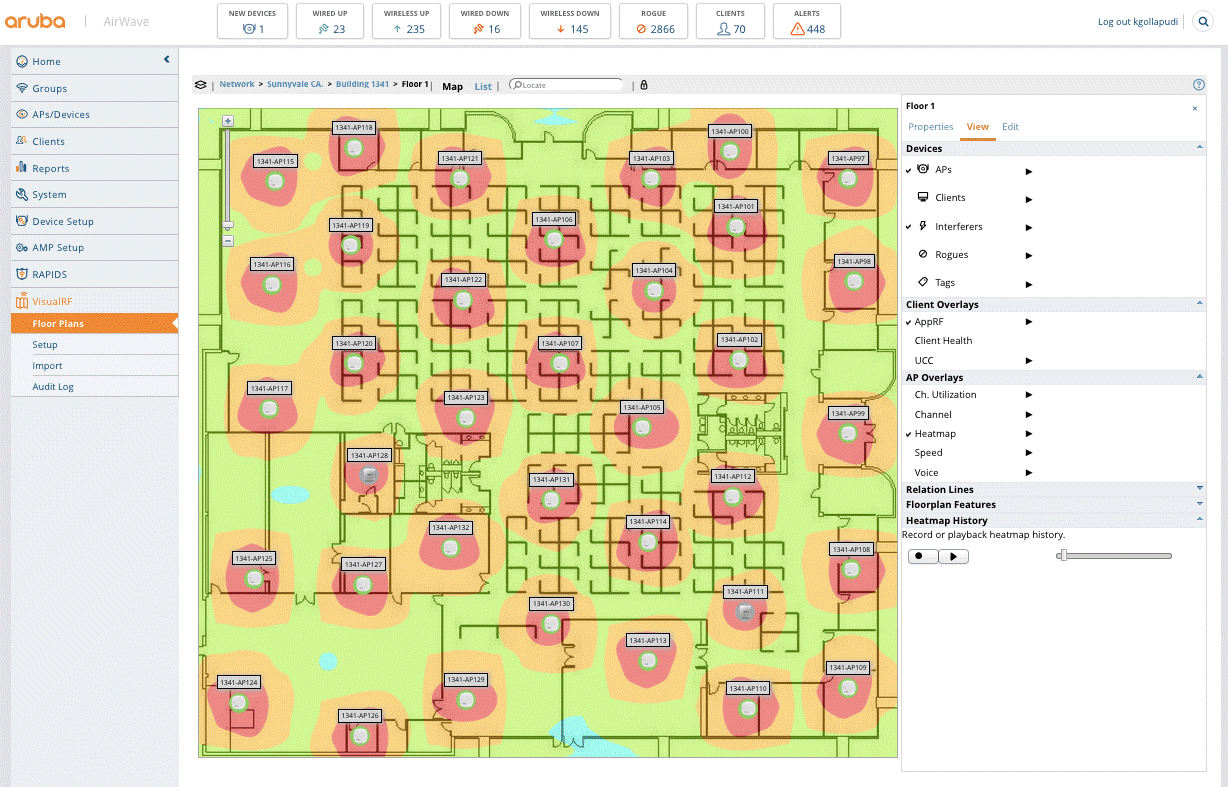
An AirWave RF heatmap indicating the WIFI signal strength within an office.
AirWave supports multi-vendor environments, discovering and mapping devices across the entire network and allowing organizations to benefit from the superior security and management features provided by Aruba and not available with other vendor’s management products.
Securing a Complex WIFI Network
In addition to, and perhaps even more important than, performance, your WIFI network needs to be designed for security. There are a variety of factors to consider. You probably want guest access to be simple and unencrypted but completely isolated from your internal network. In contrast, your corporate users probably require encrypted communication, and selective access to network resources, based on their credentials and company policies. For example, employees in the accounting department need access to the accounting systems but may not need to access the customer database.
To properly secure your network, you need network access control (NAC) tools that work with your wireless and wired technology. A NAC solution identifies users and devices, assigns policies accordingly, and enforces those policies. For example, a NAC solution could identify an accounting employee accessing the network from their laptop WIFI connection and allow access to the accounting systems. But the same employee, accessing the network from their smartphone would not be granted access to the accounting system.
At IIS, we recommend implementing the IEEE 802.1X standard protocol for port-based Network Access Control (PNAC). It is the part of the IEEE 802.1 group of networking protocols that provides an authentication mechanism for devices attempting to connect to a LAN or WLAN. It is called “port-based” because the user device wishing to connect to a port (either wireless or wired) must provide credentials and/or a certificate to an authenticator that allocates the port. These credentials are forwarded to an authentication server for validation.
The 802.1X standard defines a client-server-based access control and authentication protocol that prevents unauthorized clients from connecting to a LAN or WLAN through publicly accessible ports unless they are properly authenticated. The authentication server authenticates each client connected to a switch port or wireless access point before making available any services offered by the network.
Based on credentials and device type, access can be granted to specific virtual LANs (VLANs) and restricted from others. Leveraging 802.1X, access based on VLANs can be automatically controlled thus simplifying many aspects of network administration. For example, the time required to implement moves, adds, and changes (MAC) can be significantly reduced by eliminating the need for wiring, patching and network reconfiguration. A department moving floors within a building, for example, may experience downtime while the network is reconfigured to that their devices maintain proper access in their new locations. Taking advantage of 802.1X and VLANs eliminates this problem by assigning the user to the proper VLAN based on their credentials and device type, instead of its physical location on the network.
HPE Aruba ClearPass Provides Tools for Comprehensive WIFI Security
While AirWave is our tool of choice for configuration and performance monitoring, we use HPE Aruba ClearPass to manage WIFI security. ClearPass provides dynamic role-based access control to manage and enforce security profiles across wired and wireless networks.
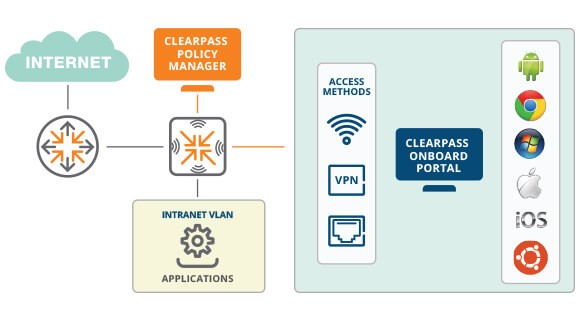 ClearPass authenticates mobile device users and enforces access policies.
ClearPass authenticates mobile device users and enforces access policies.ClearPass automatically configures and provisions mobile devices (e.g., laptops, tablets, smartphones) enabling secure connectivity to 802.1X-enabled networks with minimal onboarding support required from your IT organization. When a user connects a new device to the network, the ClearPass Onboard portal dynamically detects the device’s operating system and guides the user through the appropriate onboarding steps. This automation enables organizations to successfully implement “bring your own device” (BYOD) initiatives without straining IT support resources.
In addition to streamlining connectivity, ClearPass implements comprehensive access policies to keep your systems and data secure. Centrally-defined policies limit the types of devices that can be on-boarded and define which users can onboard devices. A centrally managed administrator portal allows IT to configure device certificates and trust details, network access, VPN, and health check settings and authentication protocols. IT staff can also define the number of devices that can be on-boarded per user and how long their certificates are valid.
IoT requires fine-grained security policies, but the enormous number of devices coming online means you need a tool like ClearPass to stay on top of access controls. While your thermostat may now have an IP address, it requires very little network access compared with a user laptop, or even a security camera that provides a video feed to various devices across the network. ClearPass can differentiate between a thermostat, a security camera, and a laptop, and apply baseline policies accordingly. Because of its ability to detect device types, ClearPass is significantly less vulnerable to MAC spoofing attacks. For example, even if a hacker pulled a MAC address off a camera and used it on their laptop, ClearPass would recognize that the laptop was not actually an authorized camera and deny access.
In addition, ClearPass can integrate with 802.1X-enabled networks where users or computers authenticate against a user database or domain such as Microsoft Active Directory to provide access control to network resources and data.
IIS – Your WIFI Solutions Partner
International Integrated Solutions (IIS) is a consultant, integrator, and managed services provider with deep expertise in network design and implementation. We have considerable experience working with the HPE Aruba AirWave and ClearPass tools. IIS is a distinguished HPE partner, winning HPE Global Partner of the Year in 2016 and Arrow’s North American Reseller Partner of the Year in 2017.
Having solved a myriad of problems for hundreds of customers, IIS brings a holistic view of the datacenter and can work with you to design and implement wireless solutions that work well with the rest of your infrastructure. When setting up or redesigning your WIFI network, IIS can help you:
- Assess end-user needs including employees and guests.
- Evaluate a new office environment and optimize access points.
- Create security profiles and priorities for end-users and devices.
- Design, implement, and support your wireless network.
- Monitor network security and proactively work to avoid outages.
- Arrange financing to provide wireless networking as an operational expense, avoiding capital outlays for equipment purchases.








